Hackers can use smartphones to tap into your 3D printer
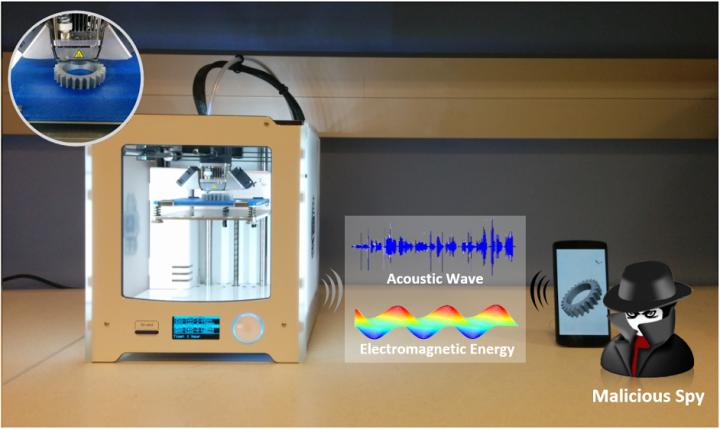
A new study conducted at the University of Buffalo has proven that hackers may be able to break into your 3D printer using a smartphone to measure leaked energy and acoustic waves.
The study revealed security vulnerabilities of 3D printing, and showed that a simple smartphone was capable of stealing sensitive data.
“Many companies are betting on 3-D printing to revolutionize their businesses, but there are still security unknowns associated with these machines that leave intellectual property vulnerable,” said Wenyao Xu, PhD, assistant professor in UB’s Department of Computer Science and Engineering, and the study’s lead author.
Unlike traditional security hacks, the researchers did not simulate a cyberattack since most 3D printers these days encompass protective measures for types of threats. Instead, they programmed an ordinary smartphone’s built-in sensors to electromagnetic energy and acoustic waves that emanate from 3D printers. The sensors are able to detect the locations of the printer’s nozzle as it moves to create the object that it’s printing.
The smartphone, which was 20 centimeters away from the printer, was able to gather enough data to for the researchers to replicate printing a simple object, such as a door stop, with a 94% accuracy rate. For complex objects, such as an automotive part or medical device, the accuracy rate was lower but still above 90%.
“The tests show that smartphones are quite capable of retrieving enough data to put sensitive information at risk,” said Kui Ren, PhD, professor in UB’s Department of Computer Science and Engineering, a co-author of the study.
According to the team, the bulk of the information was extracted from the electromagnetic waves, which accounted for about 80% of the useful data. The remaining data came from acoustic waves.
The results are important because, as the 3D-printing industry continues to progress and find its way into many important manufacturing areas, anyone with a smartphone (think disgruntled employee or industrial spy) is capable of stealing intellectual property.
“Smartphones are so common that industries may let their guard down, thus creating a situation where intellectual property is ripe for theft,” said Chi Zhou, PhD, assistant professor in UB’s Department of Industrial and Systems Engineering, another study co-author.
So how do we make 3D printers more secure?
The researchers suggest some security options for 3D printers. One such option is to keep smartphones significant distance away from 3D printers. The ability to obtain accurate data for simple objects diminished to 87% at 30 centimeters, and 66% at 40 centimeters, according to the study.
Another option is to increase print speeds. They say that new materials may allow 3D printers to work faster, and therefore make it more difficult for smartphone sensors to pick up the print nozzle’s movement.
Other ideas included software-based solutions, such as programming the printer to operate at different speeds, and hardware-based ideas, such as acoustic and electromagnetic shields.
Xu and collaborators will present the research, “My Smartphone Knows What You Print: Exploring Smartphone-based Side-channel Attacks Against 3D Printers,” at the Association for Computing Machinery’s 23rd annual Conference on Computer and Communications Security in October in Austria.

Comments are closed, but trackbacks and pingbacks are open.